Now we can begin to explore some of these services, a lot of them are pretty common (ftp, telnet, http, etc) where others are a little weird. Let's get poking. (you can use the -A option in Nmap to gather a vast amount of information regarding each service, but since I'll be getting Nessus going in a moment, I'm going to skip that for now).
I'm going do the following one port at a time (if possible) to exhaust every option for the purpose of practice. But first, lets find some vulnerabilities, we can do this in a couple different ways. We can manually search for vulnerabilities based on the services running. We can load up Nessus, Nexpose, or OpenVAS to automatically scan for vulnerabilities; I'll be using Nessus.
 |
| A nice colour-coded list of all the things Nessus found. |
Nessus is capable of integrating to Metasploit, however I had some issues getting that working so we're going to just side-step that for now. Above you can see a snippet of the vulnerabilities that Nessus found in our target - there's quite a lot.
As I said, we're going to be going one port at a time, so lets find out what's up with our FTP services (port 21). Unfortunately it looks like Nessus wasn't capable of finding any exploit on the service (vsftpd v2.3.4) so let's do a quick search on exploit-db to see if we can find anything.
 |
| Service fingerprint result from Nmap |
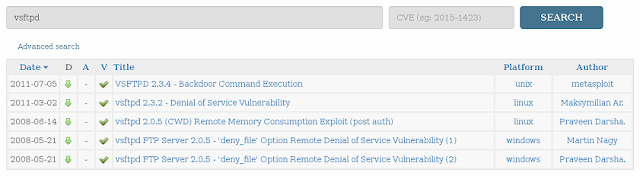 |
| Our search results from exploit-db. |
 |
| And there she is. |
For more information about the module itself, you can take a look at Rapid7's database (these are the guys who make Metasploit and Nexpose); it's also a pretty good database for looking for vulnerabilities. I'm going to be going over attacking and exploitation in a separate post.
Next up is SSH.
 |
| Vulnerabilities filtered by "SSH" |
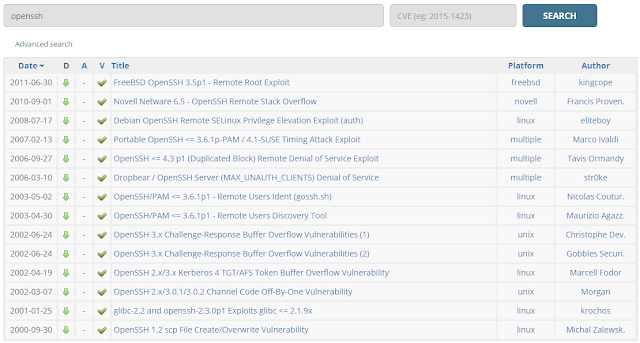
We can see that Nessus did indeed find two usable exploits regarding SSH, before we continue lets do a quick search on exploit-db again using the SSH service running on the target machine to be safe.
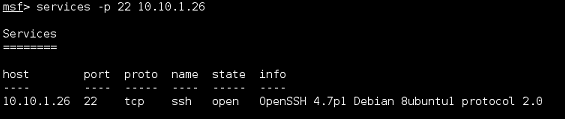 |
| We can filter by port when using the services command. |
None of these really stand out for the version we're attacking, so lets just try our luck with the two Nessus dug up.
The right hand side of Nessus (once viewing the vulnerability itself) gives us some information regarding it. When it was found, when it was patch, whether or not exploits are available and what software can take advantage of it. But the piece that interests us (especially since Metasploit isn't listed here) is that CVE number. Lets punch that into exploit-db and see if anyone's scripted an attack we can use.
 |
| WarCat team's exploit for this CVE. |
And we're in luck! We found a python script that'll attempt to brute force the SSH keys.
Next is SMTP, port 25, the target machine is using Postfix. Nmap didn't reveal too much information about the service running on the target, only that it was Postfix; this is a good chance (and reason) to enumerate the service. Enumeration can (potentially) tell us a lot of information about the service (and target). Everything from what version it's running on, to possibly what user accounts are on the mail server. Luckily, as usual, Metasploit has a module for this.
We managed to grab some usernames off the service, but still don't know what version it's running! Argh. Also should note that when Metasploit finds information through it's modules, it conveniently adds it to the database for us!
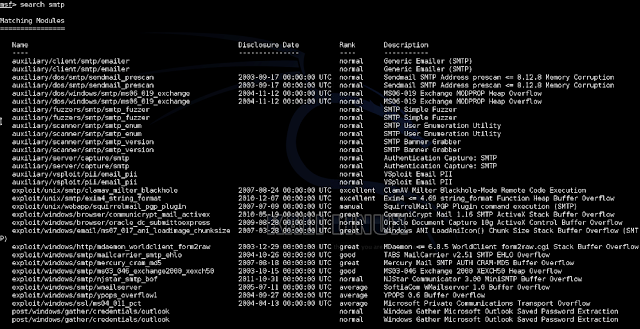
Since we don't have any leads on specific vulnerabilities to exploit, we can do two searches within Metasploit to see if she has anything to offer. The first being for Postfix specifically, the second for just SMTP.
It's not surprising that something as generic as SMTP for a search string is going to result in a large number of available modules. A lot of these are Windows-specific but I can see a few Unix ones we can attempt along with the Postfix-only exploit.
Next is SMTP, port 25, the target machine is using Postfix. Nmap didn't reveal too much information about the service running on the target, only that it was Postfix; this is a good chance (and reason) to enumerate the service. Enumeration can (potentially) tell us a lot of information about the service (and target). Everything from what version it's running on, to possibly what user accounts are on the mail server. Luckily, as usual, Metasploit has a module for this.
 |
| Found some usernames! |
Since we don't have any leads on specific vulnerabilities to exploit, we can do two searches within Metasploit to see if she has anything to offer. The first being for Postfix specifically, the second for just SMTP.



No comments:
Post a Comment