IBM has been saying since around 2012 that they integrate with Palo Alto for Layer 2 Netflow informatiion. Well an old QRadar I tested it on, did no such things; it actually stripped the Palo Alto-specific fields out of the payload. I read a lot of forums online saying the same thing. Luckily I had access to a brand new 7.2.6 demo VM and it works...sort of. The important thing is that it displays the full payload of the Netflow packet.
IBM provides a Security Content Pack for Palo Alto which as far as I can tell is useless. To get the data into QRadar properly we'll need to make custom fields (note that the "Application" field that QRadar uses port-based look ups will still be present in the log information).
Firstly, we'll need to set up a Netflow profile on the Palo Alto to point to the QRadar; make sure you check PAN-OS Field Types as this allows for User-ID and App-ID information to be sent. Also be sure to include a policy if they’re in different zones to permit the traffic.
IBM provides a Security Content Pack for Palo Alto which as far as I can tell is useless. To get the data into QRadar properly we'll need to make custom fields (note that the "Application" field that QRadar uses port-based look ups will still be present in the log information).
Firstly, we'll need to set up a Netflow profile on the Palo Alto to point to the QRadar; make sure you check PAN-OS Field Types as this allows for User-ID and App-ID information to be sent. Also be sure to include a policy if they’re in different zones to permit the traffic.
Apply the profile to interfaces. Make sure these are inside interfaces and not web facing unless you’ll
end up getting a lot of noise.
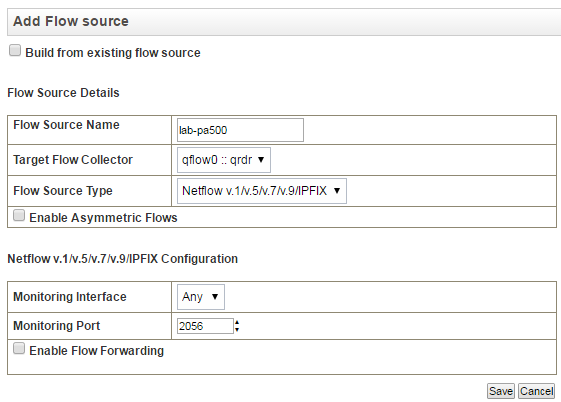
In the QRadar, add the Palo Alto device as a Flow Source,
use the same port you specified in your Netflow profile on the Palo Alto
Once added you should see a bunch of flow traffic coming
into the “Network Activity” tab in QRadar.
If you go into one of them, you’ll notice that QRadar
doesn’t map Palo Alto’s Layer 7 information (App-ID and User-ID) correctly or
at all for that matter. The current application being indexed for each flow is
a port-based lookup that the QRadar performs.
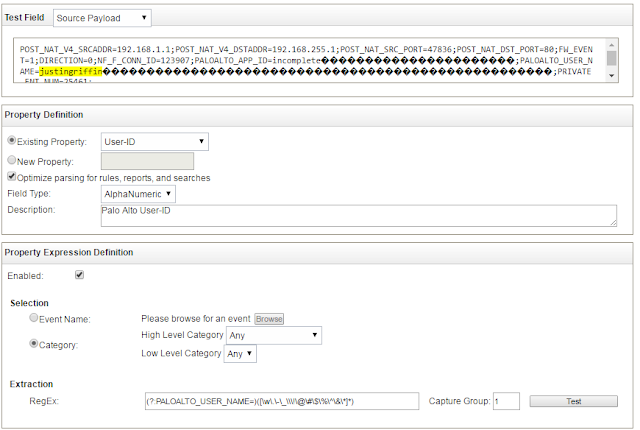
To get around this we can create two Custom Flow Properties. Navigate to Admin> Flows> Custom Flow Properties and
click Add at the top and fill out the little wizard-esque window with the appropriate
fields, mine is below.
The regex I wrote for this should catch all alphanumeric
character as well as generally used special characters as well as periods,
hyphens, underscores, and backslashes (to accommodate the domain name being
included in the username). I can’t imagine any other characters showing up in
this field.
The Regex for User-ID fields: (?:PALOALTO_USER_NAME=)([\w\.\-\_\\\!\@\#\$\%\^\&\*]*)
You can go ahead and do the same for the application ID;
luckily only alpha and hyphens will show up here because that’s all Palo Alto
uses for its naming. I included underscores as well because application
signatures can be user-created and they may end up using them.
The Regex for App-ID fields: (?:PALOALTO_APP_ID=)([A-Za-z\-\_]*)
Once that’s completed, you can go back to your Network
Activity and see the applications and users being mapped correctly.
Now that we’re indexing App-ID and User-ID, we can use them
for reporting and graphs. Some example of use cases would be:
- Top-Talkers by App or User
- Reference set of Users for use with rules
- Behavior analysis of application use (thresholds)
- Offenses based on unpermitted applications (if app is in not allowed reference set and from user x then fire offense)